An organization requires the following to be achieved between the finance and marketing departments:
✑ Allow HTTPS/HTTP.
✑ Disable FTP and SMB traffic.
Which of the following is the MOST suitable method to meet the requirements?
An organization requires the following to be achieved between the finance and marketing departments:
✑ Allow HTTPS/HTTP.
✑ Disable FTP and SMB traffic.
Which of the following is the MOST suitable method to meet the requirements?
The most suitable method to meet the requirements of allowing HTTPS/HTTP traffic and disabling FTP and SMB traffic between the finance and marketing departments is to configure an Access Control List (ACL) between the VLANs. ACLs can be used to permit or deny traffic based on protocol and ports, ensuring that only the desired protocols (HTTPS and HTTP) are allowed while blocking any unwanted traffic (FTP and SMB).
A systems administrator is building a new virtualization cluster. The cluster consists of five virtual hosts, which each have flash and spinning disks. This storage is shared among all the virtual hosts, where a virtual machine running on one host may store data on another host.
This is an example of:
The scenario described involves a cluster of virtual hosts that share storage internally, without an external storage server. Hyperconverged storage integrates compute, storage, and networking into a single system and allows for the creation of a virtual pool of storage that can be shared among the hosts. This matches the description provided in the question.
A company is utilizing a private cloud solution that is hosted within its datacenter. The company wants to launch a new business application, which requires the resources below:
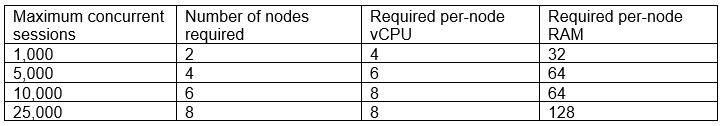
The current private cloud has 30 vCPUs and 512GB RAM available. The company is looking for a quick solution to launch this application, with expected maximum sessions to be close to 24,000 at launch and an average of approximately 5,000 sessions.
Which of the following solutions would help the company accommodate the new workload in the SHORTEST amount of time and with the maximum financial benefits?
The current private cloud setup has 30 vCPUs and 512GB of RAM available. For the expected maximum sessions of close to 24,000, the application requires 8 nodes with 8 vCPUs and 128GB of RAM each. This amounts to a total requirement of 64 vCPUs and 1024GB of RAM, which the private cloud cannot support on its own. However, the average sessions are approximately 5,000, which requires 4 nodes with 6 vCPUs and 64GB of RAM each, amounting to 24 vCPUs and 256GB of RAM, which is within the current capacity. Setting up cloud bursting allows the private cloud to handle the average load while leveraging additional public cloud resources to manage peak loads, thus providing a quick and financially beneficial solution.
A systems administrator recently upgraded the processors in a web application host. Upon the next login, the administrator sees a new alert regarding the license being out of compliance.
Which of the following licensing models is the application MOST likely using?
The alert regarding the license being out of compliance after upgrading the processors suggests that the licensing is based on the number of cores in the system. Core-based licensing typically requires a license for each core in the processor. When additional cores are added through an upgrade, it can cause the system to go out of compliance if there aren't enough licenses to cover the new core count.
A systems administrator is informed that a database server containing PHI and PII is unencrypted. The environment does not support VM encryption, nor does it have a key management system. The server needs to be able to be rebooted for patching without manual intervention.
Which of the following will BEST resolve this issue?
The best solution to resolve the issue of an unencrypted database server containing PHI and PII, while ensuring the server can be rebooted for patching without manual intervention, is to enable volume encryption on the storage. Volume encryption protects data at rest, ensuring that even if the physical storage is lost or stolen, the data remains encrypted and secure. This solution meets the requirement without needing additional infrastructure like a key management system or support for VM encryption.