A Chief Information Security Officer (CISO) is evaluating the company's security management program. The CISO needs to locate all the assets with identified deviations and mitigation measures. Which of the following would help the CISO with these requirements?
A risk register is a comprehensive document that tracks all identified risks, including assets with deviations and their mitigation measures. It includes a description of each risk, the impact it could have on the business, and the likelihood of its occurrence. Importantly, the risk register also documents the controls or measures in place to mitigate these risks, making it the most suitable tool for the CISO to locate all assets with identified deviations and associated mitigations.
A cloud engineer is responsible for managing a public cloud environment. There is currently one virtual network that is used to host the servers in the cloud environment. The environment is rapidly growing, and the network does not have any more available IP addresses. Which of the following should the engineer do to accommodate additional servers in this environment?
The engineer should create a VPC (Virtual Private Cloud) and peer the networks. This approach allows for the creation of a new network with its own IP address space, which can then be linked (or peered) with the existing network. This will effectively expand the available IP address space, accommodating additional servers. The other options do not address the problem of running out of IP addresses: implementing dynamic routing and enabling DHCP do not increase the IP address pool, and obtaining a new IPAM subscription helps manage IP addresses but doesn't provide additional addresses needed to host more servers.
A system administrator is migrating a bare-metal server to the cloud. Which of the following types of migration should the systems administrator perform to accomplish this task?
To migrate a bare-metal server, which is a physical server, to a cloud environment, the migration involves converting the physical server to a virtual machine. This process is known as Physical to Virtual (P2V) migration.
A company is utilizing a private cloud solution that is hosted within its datacenter. The company wants to launch a new business application, which requires the resources below:
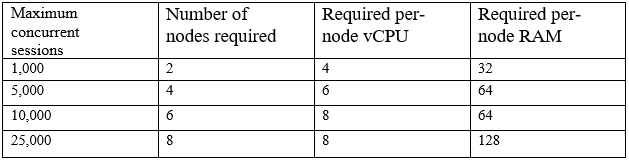
The current private cloud has 30 vCPUs and 512GB RAM available. The company is looking for a quick solution to launch this application, with expected maximum sessions to be close to 24,000 at launch and an average of approximately 5,000 sessions. Which of the following solutions would help to company accommodate the new workload in the SHORTEST amount of time and with the maximum financial benefits?
The company needs a quick solution to accommodate a high number of concurrent sessions close to 24,000 at launch, with an average of approximately 5,000 sessions. The current private cloud resources (30 vCPUs and 512GB RAM) are not sufficient to handle the maximum expected load of close to 24,000 sessions, which requires 64 vCPUs and 1024GB RAM per the provided resource table. Adding more capacity to the private cloud or migrating all workloads to a public cloud provider would take more time and might incur higher costs. Auto-scaling within the private cloud is not feasible due to current resource limitations. Therefore, setting up cloud bursting for additional resources is the best option as it allows the company to efficiently handle the peak load by utilizing additional resources from a public cloud while maintaining the current private cloud setup.
A cloud administrator is reviewing the authentication and authorization mechanism implemented within the cloud environment. Upon review, the administrator discovers the sales group is part of the finance group, and the sales team members can access the financial application. Single sign-on is also implemented, which makes access much easier. Which of the following access control rules should be changed?
Role-based access control (RBAC) is being described in this scenario. The sales group should not be nested within the finance group if members of the sales group should not have access to the financial application. The appropriate access control rule to change is the role-based access, by adjusting the roles and permissions associated with these groups to ensure proper access restrictions.