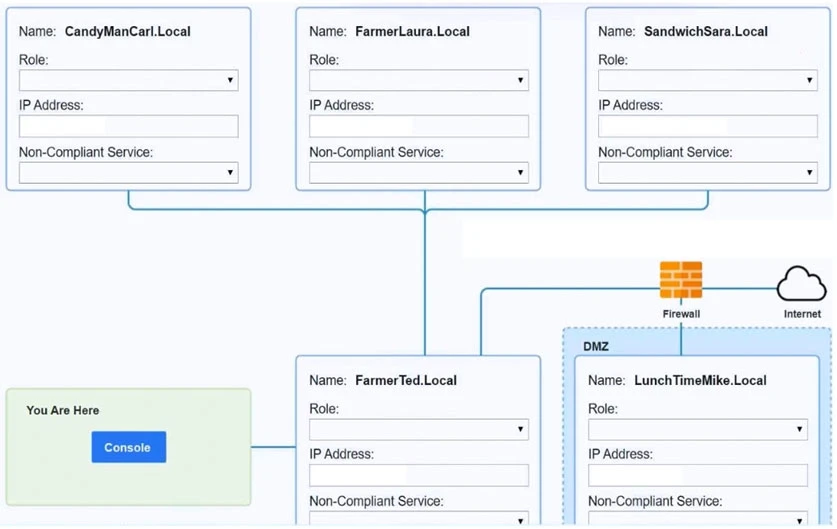
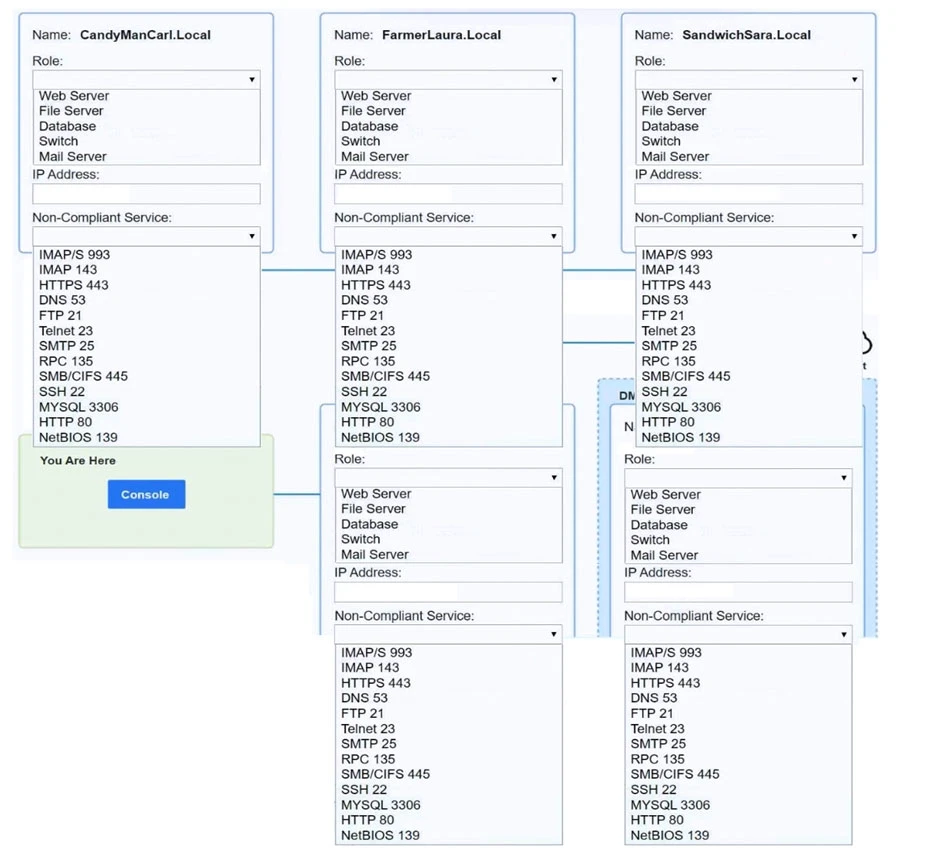
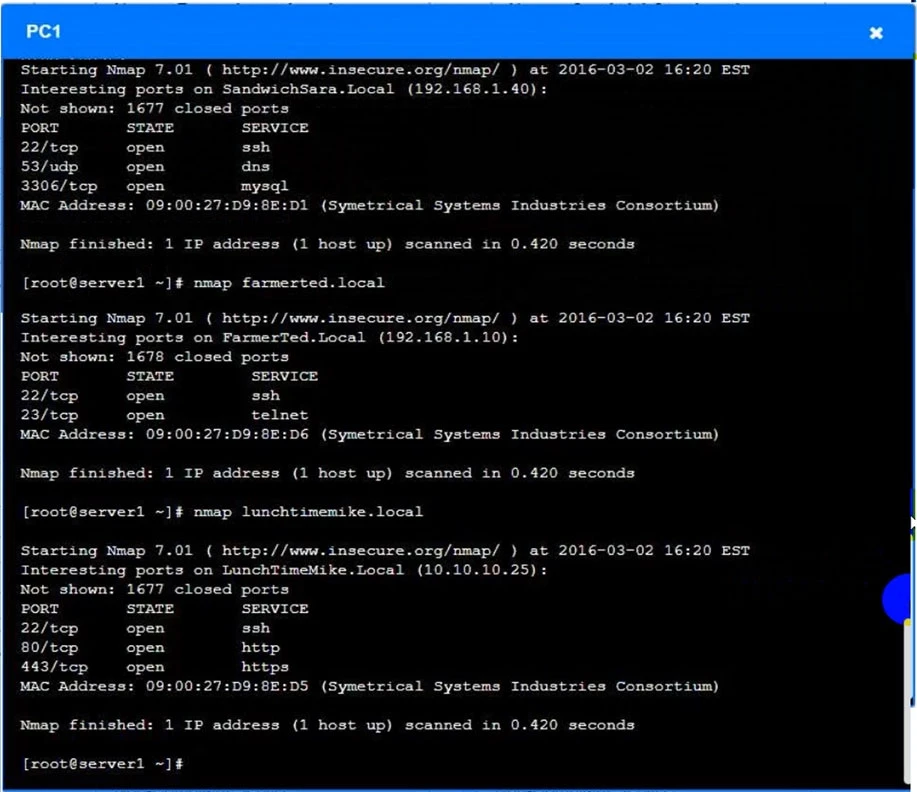
You are a penetration tester who is reviewing the system hardening guidelines for a company's distribution center. The company's hardening guidelines indicate the following:
✑ There must be one primary server or service per device.
✑ Only default ports should be used.
✑ Non-secure protocols should be disabled.
✑ The corporate Internet presence should be placed in a protected subnet.
INSTRUCTIONS -
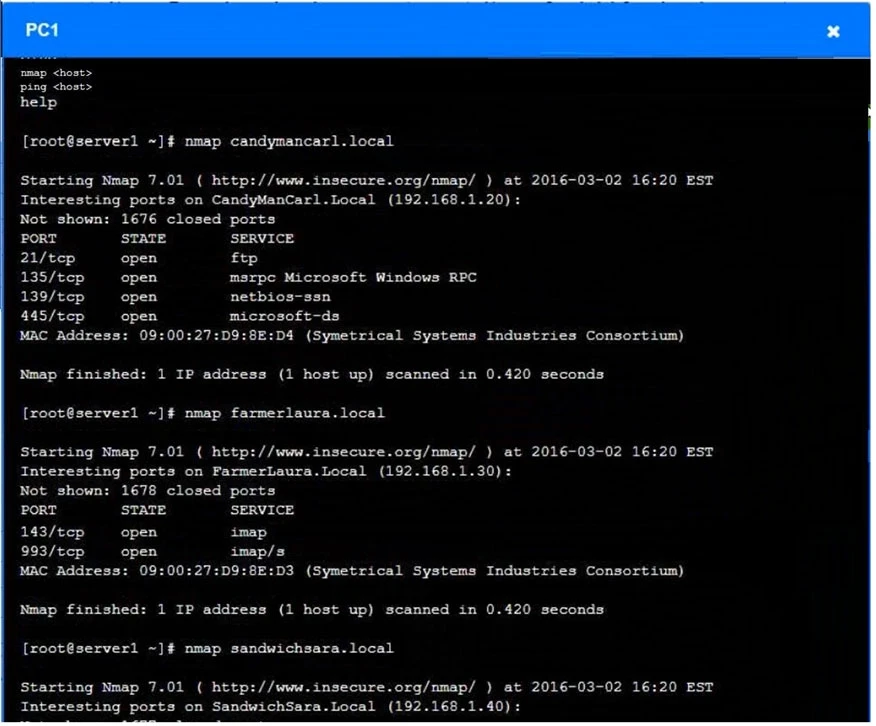
Using the tools available, discover devices on the corporate network and the services that are running on these devices.
You must determine:
✑ The IP address of each device.
✑ The primary server or service of each device.
✑ The protocols that should be disabled based on the hardening guidelines.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
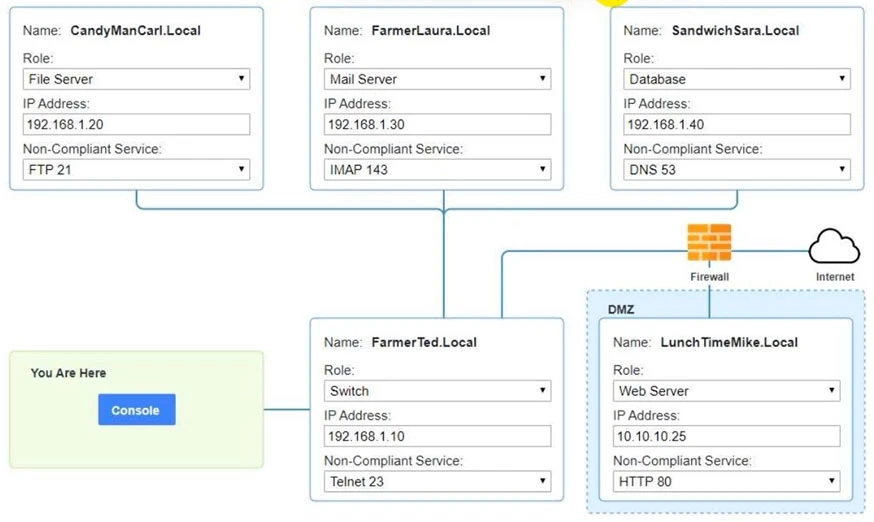
 See explanation below.
See explanation below.