To prevent SQL injection vulnerabilities, input validation and a web application firewall (WAF) should be put in place. Input validation ensures that any data sent to the server is checked for potentially malicious content, effectively mitigating the risk of SQL injection. A WAF can filter and monitor HTTP traffic to and from a web application, providing an additional layer of security by blocking malicious requests attempting to exploit SQL injection vulnerabilities.
An ISA (Interconnection Security Agreement) is a document that outlines the technical and security requirements for establishing, operating, and maintaining a secure connection between networks or systems belonging to different organizations. In the context of setting up a business-to-business VPN, this agreement would detail the security measures, protocols, and rules that both parties must adhere to, ensuring the integrity, confidentiality, and availability of the data being transmitted over the VPN.
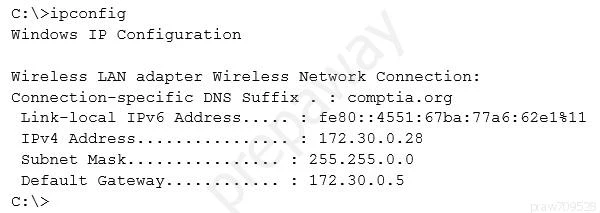
Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
To allow the PC to serve an intranet website, it needs to accept incoming traffic on port 80, which is the standard port for HTTP traffic. The ACL should permit intranet users to access the web server hosted on the PC. Given that the intranet might span multiple subnets within the 172.30.0.0/16 network, allowing traffic from any address within this subnet range to port 80 on 172.30.0.28 would enable access appropriately. So, the correct rule would be 'Allow 172.30.0.28:80 -> 172.30.0.0/16'.
Posing as a copier service technician and indicating the equipment had 'phoned home' to alert the technician for a service call is the most plausible method of social engineering in this context. A penetration tester conducting a physical assessment aims to gain physical access to a site. By posing as a service technician, the tester can appear legitimate and gain entry into the facility. This method exploits the human element of trust and perceived authority, making it an effective form of social engineering for physical security testing. Other options either do not focus on gaining physical access, or involve highly risky and illegal activities, which are unlikely to be the preferred methods in such engagements.
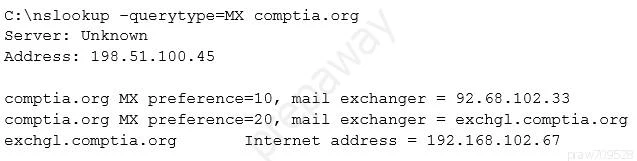
Which of the following should the penetration tester conclude about the command output?
To conclude about the command output, the fact that a private IP address (192.168.102.67) is visible in the public DNS query result indicates a misconfiguration in the DNS settings for Comptia.org. Typically, private IP addresses should not be exposed through public DNS records as they are not routable on the public Internet and are intended to be used only within private networks. Therefore, the public/private views on the Comptia.org DNS servers are misconfigured.