The physical security department received a report that an unauthorized person followed an authorized individual to enter a secured premise. The incident was documented and given to a security specialist to analyze. Which step should be taken at this stage?
In the case of an unauthorized person entering a secured premise, the most immediate step is to identify the movement of the intruder within the enterprise. This involves assessing where the intruder has been and what activities they have undertaken to understand the extent of the breach. This information is crucial for making informed decisions regarding further actions to mitigate any potential damages and to reinforce security measures effectively.
A new malware variant is discovered hidden in pirated software that is distributed on the Internet. Executives have asked for an organizational risk assessment.
The security officer is given a list of all assets. According to NIST, which two elements are missing to calculate the risk assessment? (Choose two.)
To accurately calculate a risk assessment according to NIST, two essential elements are an asset vulnerability assessment and a malware analysis report. An asset vulnerability assessment helps identify and prioritize vulnerabilities in the organization's assets, which is crucial for understanding potential impact and likelihood of threats. A malware analysis report provides detailed information about the malware, including its capabilities, attack vectors, and potential impact. These elements are essential for determining the risk to the organization's assets and the necessary mitigation strategies.

Refer to the exhibit. At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
Based on the URIs of inbound web requests, the attacker appears to be in the reconnaissance stage of the threat kill chain. During reconnaissance, attackers gather information about potential targets, including identifying vulnerabilities and weaknesses in systems and applications. The URIs provided, such as '/invoker/JMXInvokerServlet', '/CFIDE/adminapi', and others that include scripts aiming to trigger alerts and access sensitive files, suggest that the attacker is scanning for known vulnerabilities and attempting to gain information. This aligns with typical reconnaissance activities aimed at preparing for further stages of an attack.

Refer to the exhibit. How must these advisories be prioritized for handling?
Vulnerability #2 should be considered the highest priority for handling. This vulnerability allows an attacker to bypass authorization checks and access sensitive information without needing to log in, simply by reaching port 80/tcp on the affected device and having the web-based management interface enabled. This presents a broader attack surface and easier exploitation method compared to Vulnerability #1, which requires an attacker to be logged in as a high-privileges administrative user. Additionally, there are fixes available for Vulnerability #1, which reduces its urgency compared to the unpatched nature of Vulnerability #2.
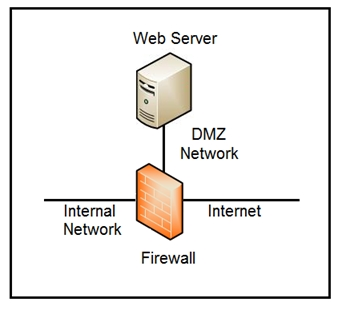
Refer to the exhibit. Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
Creating an Access Control List (ACL) on the firewall to allow only TLS 1.3 enhances security by ensuring that the web server only accepts secure, encrypted connections, reducing the risk of interception and eavesdropping. Implementing a reverse proxy server in the DMZ network serves as an additional intermediary layer that can filter traffic, cache data, and conceal the web server's IP address, offering extra protection against direct internet attacks.