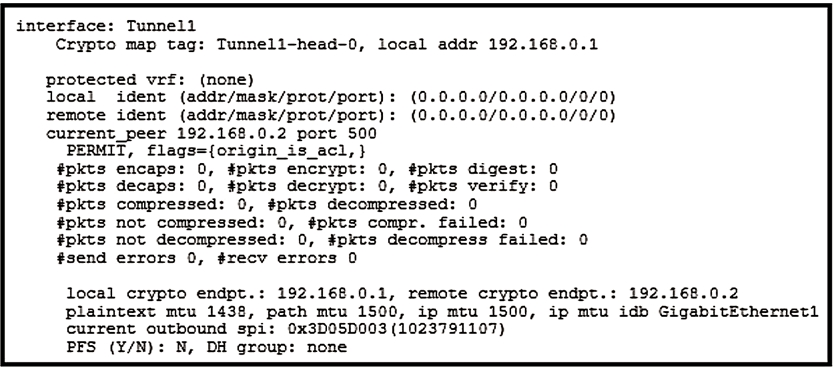
Refer to the exhibit. Which two tunnel types produce the show crypto ipsec sa output seen in the exhibit? (Choose two.)

Refer to the exhibit. Which two tunnel types produce the show crypto ipsec sa output seen in the exhibit? (Choose two.)
The exhibit displays the output from the 'show crypto ipsec sa' command. The characteristics in the output point towards tunnel interfaces that use IPsec. Specifically, the 'local ident' and 'remote ident' fields showing 0.0.0.0/0.0.0.0/0/0 indicate a raw IPsec tunnel setup utilized by Virtual Tunnel Interface (VTI) and FlexVPN. Moreover, the exhibit does not indicate any references to protocol 47, which would be present if it were a GRE tunnel. Therefore, the correct tunnel types producing this output are FlexVPN and VTI.
Which two changes must be made in order to migrate from DMVPN Phase 2 to Phase 3 when EIGRP is configured? (Choose two.)
To migrate from DMVPN Phase 2 to Phase 3 when EIGRP is configured, it is required to enable EIGRP next-hop-self on the hub and add NHRP redirects on the hub. In DMVPN Phase 2, next-hop-self is typically disabled on the hub to facilitate spoke-to-spoke communication. Moving to Phase 3 necessitates re-enabling this feature to ensure proper routing. Furthermore, adding NHRP redirects on the hub is essential as it allows the hub to inform the spokes about the optimal path for direct communication, thus enhancing efficiency.
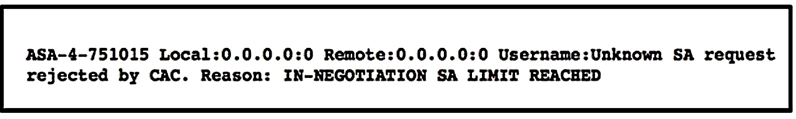
Refer to the exhibit. A customer cannot establish an IKEv2 site-to-site VPN tunnel between two Cisco ASA devices. Based on the syslog message, which action brings up the VPN tunnel?
The syslog message indicates that the Security Association (SA) request was rejected because the in-negotiation SA limit has been reached. To resolve this issue, the maximum in-negotiation SA limit on the local Cisco ASA needs to be increased. This will allow more SAs to be negotiated simultaneously, thereby bringing up the VPN tunnel.
Which two parameters help to map a VPN session to a tunnel group without using the tunnel-group list? (Choose two.)
To map a VPN session to a tunnel group without using the tunnel-group list, two effective parameters are certificate map and group-url. Certificate mapping allows you to associate user attributes to specific connection profiles based on the information present in the user's certificate. Group-url enables users to connect to a specific group URL, which is directly associated with a particular tunnel group. This method bypasses the need for the tunnel-group list and directly assigns the session to the intended tunnel group.
Which method dynamically installs the network routes for remote tunnel endpoints?
Reverse route injection (RRI) is the method that dynamically installs the network routes for remote tunnel endpoints. RRI allows the router to automatically learn the routes for the remote networks and install these routes into the routing table. This feature is commonly used in VPN environments, where it eliminates the need for manual configuration and maintenance of routes for remote networks.