HOTSPOT -
You have an Azure subscription that contains the resources shown in the following table.
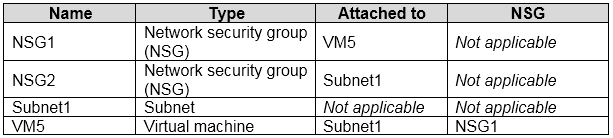
An IP address of 10.1.0.4 is assigned to VM5. VM5 does not have a public IP address.
VM5 has just in time (JIT) VM access configured as shown in the following exhibit.
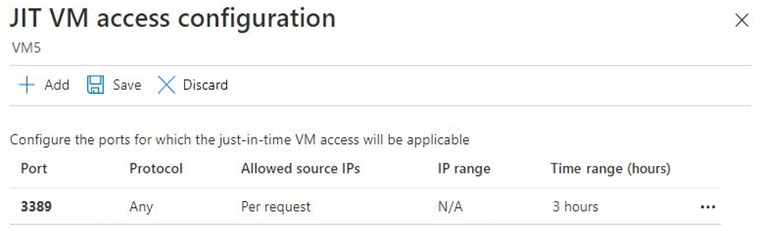
You enable JIT VM access for VM5.
NSG1 has the inbound rules shown in the following exhibit.

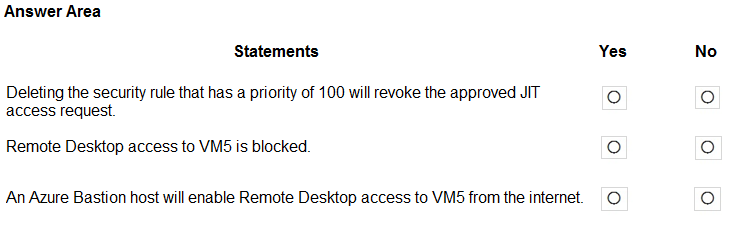
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: