You have an Azure subscription linked to an Azure Active Directory tenant. The tenant includes a user account named User1.
You need to ensure that User1 can assign a policy to the tenant root management group.
What should you do?
You have an Azure subscription linked to an Azure Active Directory tenant. The tenant includes a user account named User1.
You need to ensure that User1 can assign a policy to the tenant root management group.
What should you do?
B
The following chart shows the list of roles and the supported actions on management groups.
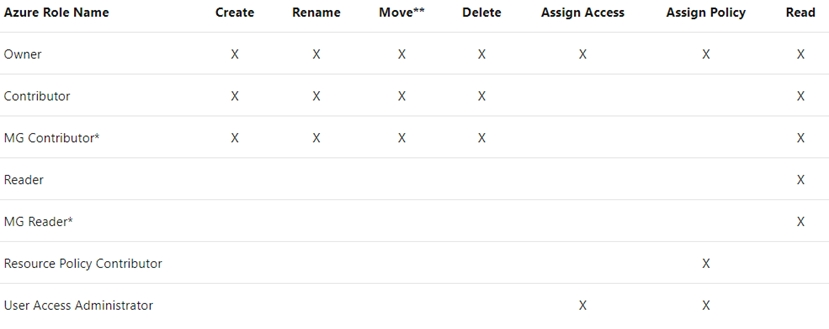
Note:
Each directory is given a single top-level management group called the "Root" management group. This root management group is built into the hierarchy to have all management groups and subscriptions fold up to it. This root management group allows for global policies and Azure role assignments to be applied at the directory level. The Azure AD Global Administrator needs to elevate themselves to the User Access Administrator role of this root group initially. After elevating access, the administrator can assign any Azure role to other directory users or groups to manage the hierarchy. As administrator, you can assign your own account as owner of the root management group.
Reference:
https://docs.microsoft.com/en-us/azure/governance/management-groups/overview
Correct Answer: C No one is given default access to the root management group. Azure AD Global Administrators are the only users that can elevate themselves to gain access. Once they have access to the root management group, the global administrators can assign any Azure role to other users to manage it. Reference: https://docs.microsoft.com/en-us/azure/governance/management-groups/overview#important-facts-about-the-root-management-group https://docs.microsoft.com/en-us/azure/governance/management-groups/overview
mlantonis is correct - the answer here should be C. Assign the Global administrator... Assigning the owner role to the "tenant root" (not the subscription) or the resource policy contributor role wouldve been enough access for user1 but that is not one of the options in the choices. so the only choice that works is C.
Answer is C. Just tested in the lab.
Why would you assume that USER1 needs to be the Global Administrator, or is a Global Administrator, rather than assuming that I am the Global Administrator? Assuming I am the Global Administrator, and that I have granted myself User Access Administrator, then using the least privileged best practice I would pick B and assign User1 any other role, like Owner, rather than Global Administrator. Granting everyone/anyone GA to assign policies seems like a horrible idea. The Owner role is enough to assign policy to the root management group. There is no need to assign User1 Global Administrator so that User1 can grant themselves the role.
It cannot be A or B simply because subscriptions are underneath Management groups. So doing any thing to those does not fix the issue. Cannot be D since that is creating a new management group. B is the only answer that comes close. Your concerns about assigning a GA noted but no other answer is provided that would alleviate your concerns.
@Alscoran, you say B is close or you mean C is close?
Does anyone have contributor access then please help me.
Ans C: No one is given default access to the root management group. Azure AD Global Administrators are the only users that can elevate themselves to gain access. Once they have access to the root management group, the global administrators can assign any Azure role to other users to manage it.
No, the correctly answer is B. C is to control Azure AD (Global Administrators), not to control Management group. If you need to control Management group, use: Access control (IAM)> Add role assignment> Role> Owner or Contributor (in this case you will use Owner). Don't exist "Global Administrators" inside of Access control (IAM)> Add role assignment. The link between Azure AD and Management group will allow that you choose an user of your Azure AD, but not will inherit Azure AD role.
This is right. Check the chart in this link. Owners assign policy. https://docs.microsoft.com/en-us/azure/governance/management-groups/overview#management-group-access
How can it be right when the question specifies the root management group and B specifies a child subscription? The only way to ensure they can make changes to the root management group is to make them a GA on the tenant and then they can assign themselves the owner permissions to that group.
B cant be right because the owner access is given at subscription level only.
not true. yo0u can give the owner roll to the Tenant Root Group in the Access control (IAM) blade > Role assignments > Add
I agree. Basically there are 3 RBAC methods. They are for 1) Azure AD 2) Azure resources including Management group 3) Classic (used by Subscription)
The answer is C, the user should be a GA and then elevate themselves to gain access.
True. https://docs.microsoft.com/en-us/azure/governance/management-groups/overview
ChatGPT4 says C
Just verified this. Owner of the subscription is not enough to assign a policy at the root management group. The user needs to have at least the "Microsoft.Authorization/policyAssignments/write"-Permission and probably a couple more read permissions at the root management group. So given the options answer C fulfills this.
C is right
Correct Answer: C reasoning: becuase
Answer should be C
Doc says: The Microsoft official documentation (https://learn.microsoft.com/en-us/azure/governance/management-groups/overview#root-management-group-for-each-directory) says that: "The Azure AD Global Administrator needs to elevate themselves to the User Access Administrator role of this root group initially. " So I would for C but I tryed in lab it doesn't work because Global Administrator can elevate himself to User Access Administrator but the scope of these roles isn't on, or inherited to Tenant Root Management Group so the user1 can't access the overview page of Tenant Root Management Group neither the Access Control (IAM) blade and in this way it'is impossible to him to to assign any policy. The only two possible ways are: 1) Grant User Access Administrator and Resource Policy Contributor to User1 on Tenant Root Management Group 2) Assign Owner role to User1 on Tenant Root Management Group Only After one of these, User1 is able to apply policy to the Tenant Root Management Group.
Out of the available options, only C will work since the root management group is higher than the subscription in the hierarchy, and the user must be either made an Owner of the management group (option not provided), or be able to make themselves an Owner on it.
D. Create a new management group and delegate User1 as the owner of the new management group. Assigning ownership of a new management group to User1 allows them to manage policies and access controls within that management group, including assigning policies to the tenant root management group if necessary. This approach provides User1 with the necessary permissions to manage policies effectively while maintaining proper governance over Azure resources.
To ensure that User1 can assign a policy to the tenant root management group, you should choose Option C: Assign the Global administrator role to User1, and then instruct User1 to configure access management for Azure resources. The Global Administrator role in Azure Active Directory has permissions to all administrative features. This role is the most powerful role, and it can assign policies to the tenant root management group. The Owner role for the Azure subscription does not have this level of access. Therefore, options A and B would not meet the requirements. Option D is not relevant as it involves creating a new management group, which is not necessary in this case.
By assigning the Owner role for the Azure subscription to User1, they will have the necessary permissions to manage resources within the subscription, including assigning policies to management groups. Then, instructing User1 to configure access management for Azure resources will allow them to assign policies to the tenant root management group.
It depends. If the subscription is attached to a subgroup manager, the user cannot modify the root group's IAM. If a subscription is attached to the root, the user can modify IAM. If the user is global, then he can gain access across all subscriptions using an "Elevate access" option. I would go with option C because it doesn't say what level the subscription is at. https://learn.microsoft.com/en-us/azure/role-based-access-control/elevate-access-global-admin?tabs=azure-portal
The correct answer is B. Assign the Owner role for the Azure subscription to User1, and then instruct User1 to configure access management for Azure resources12. To assign a policy to the tenant root management group, User1 needs to have the Microsoft.Authorization/roleAssignments/write permission, such as those provided by the Owner role12. Once User1 has the Owner role, they can configure access management for Azure resources, including assigning policies to the tenant root management group12.
management groups are on top of subscriptions ! if you set subscription owner rights to a user he will never be able to do anything else besides resources on that subscription C is the only applicable variant here
well the answer for above question is incorrect cuz we are talking about the managment level not the subscription level so i tested it the letter C is the correct answer
Although C is not a recommend practice(in more than 1 way), its the only one that would achieve the goal. Assigning owner role to the subscription wouldn't allow the user to assign policies at the root MG level, which is sitting at a higher hierarchical level than the sub (roughly the same reason why D doesn't work), with C the user can elevate himself to owner or access or policy assigner at root MG level any of which would then allow the user to assign a policy at root MG, that could apply to any MG,RG, Resource and Subscription created under that tenant.