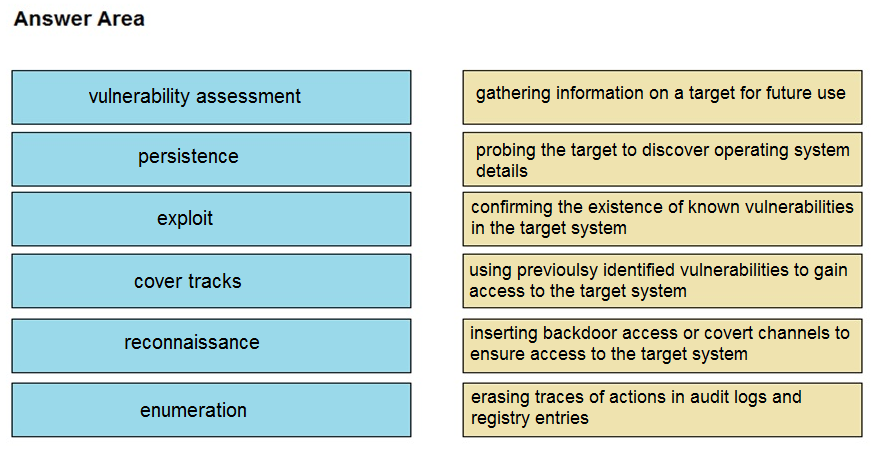
DRAG DROP -
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.
Select and Place:
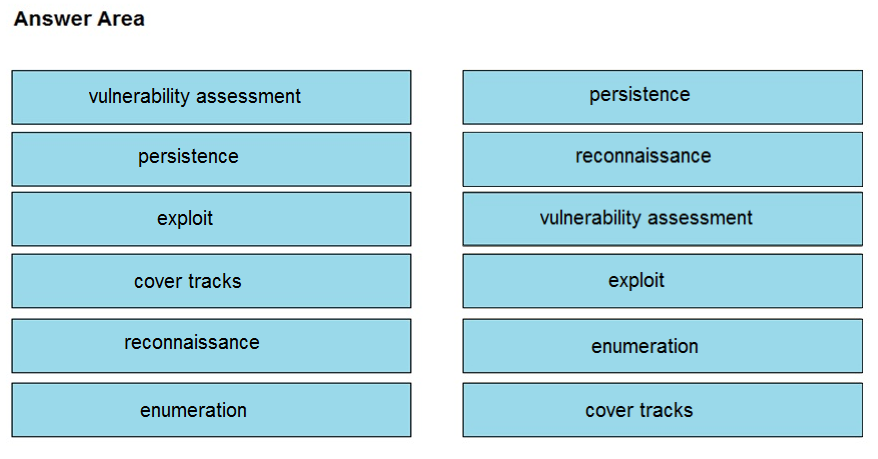
DRAG DROP -
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.
Select and Place:

Reconnaissance Enumeration Vulnerability Assessment Exploit Persistence Cover Tracks (having just taken the test I can tell you less than 5 of these 149 questions were on the test in 1/23 ! )
Can yo u Share more info ?
I think the answer is wrong. For me it should be: Vulnerability assessment - Confirming the existence of known vulnerabilities in the target system Persistence - Inserting backdoor access or covert channels to ensure access to target system Exploit - Using previously identified vulnerabilities to gain access to the target system Cover tracks - Erasing traces of actions in audit logs and registry entries Reconnaissance - Probing the target to discover operating system details Enumeration - Gathering information on a target for future use
I think you have the las two wrong. Recon gathers info from many sources not only probing the target. Enumeration focuses on probing the taget. it should be: Vulnerability assessment - Confirming the existence of known vulnerabilities in the target system Persistence - Inserting backdoor access or covert channels to ensure access to target system Exploit - Using previously identified vulnerabilities to gain access to the target system Cover tracks - Erasing traces of actions in audit logs and registry entries *Reconnaissance - Gathering information on a target for future use *Enumeration - Probing the target to discover operating system details
agree with CiscoTester
totally agree. thank you for sharing your inputs.
The selected answers are drastically WRONG. Reconnaissance -- gather info Enumeration -- probing the target Vulnerability Assessment -- confirming the existence of known vulnerabilities Persistence -- inserting backdoor access or covert channels Cover Tracks -- erasing traces Exploit -- using previously identified vulnerabilities Persistence is basically trying to make sure the target system is accessible by the attacker so the attacker makes sure they have long-term access to the target.
Jay - google DrVoIP About and please email me.
Is it support@ ??? I’d like to ask a few questions myself
took the test today but failed. This is test question.
The following matches the phases to the activities: Reconnaissance: Gathering information on a target for future use. Enumeration: Probing the target to discover operating system details. Vulnerability Assessment: Confirming the existence of non-vulnerabilities in the target system. Exploit: Using previously identified vulnerabilities to gain access to the target system. Persistence: Inserting backdoor access or covert channels to ensure access to the target system. Cover Tracks: Erasing traces of actions in audit logs and registry entries. (verified through ChatGPT)
https://attack.mitre.org/tactics/TA0043/ Reconnaissance Resource Development Initial Access Execution Persistence Privilege Escalation Defense Evasion Credential Access Discovery Lateral Movement Collection Command and Control Exfiltration