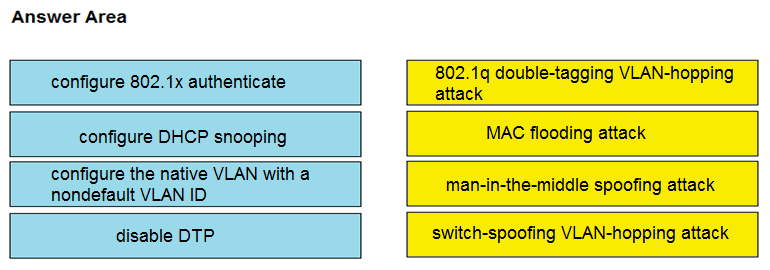
DRAG DROP -
Drag and drop the attack-mitigation techniques from the left onto the types of attack that they mitigate on the right.
Select and Place:
DRAG DROP -
Drag and drop the attack-mitigation techniques from the left onto the types of attack that they mitigate on the right.
Select and Place:

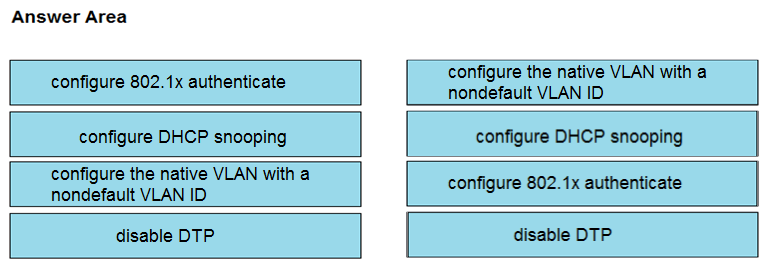
change the default vlan id => prevents double tagging configure 802.1x authenticate => prevents MAC flooding enable DHCP Snooping => prevents MITM disable DTP => prevents switch spoofing
Absolutely correct
wrong. DHCP snooping stops Rogue servers. Dynamic Arp inspection stops MITM attacks. 802.1x is to authenticate users and they dont get access until they authenticate.
Yeah but DHCP snooping needs to be configured for DAI to work.
Wrong, the original answer is correct. DHCP snooping prevents MAC flooding starvation attack, 802.1x verifies endpoint identity and prevents MITM spoofing.
Jeremy's IT Lab explained. Rogue DHCP server modifies default GW on client. make client always send packets to the rogue server to other LAN
Check the source https://www.interserver.net/tips/kb/mac-flooding-prevent/ Mac flooding is overcome by 802.1X MITM attack is overcome by DHCP Snooping Please correct the answers @Admin
the correct answer should be: the 1st and 4th are correct but the 2nd and 3rd should be swapped.
Not correct. Right answer is https://itexamanswers.net/question/drag-and-drop-the-attack-mitigation-techniques-from-the-left-onto-the-types-of-attack-that-they-mitigate-on-the-right
@sinear... that link actually gives the wrong answer. The solution posted here is correct.
technically dhcp snooping mitigates man in the middle attacks!
Thats what i chose
The answer posted to the website is wrong. 802.1x is for MAC flooding, and DHCP snooping is for MITM attacks. I just googled them both individually. Plus, that's what two other braindumps that I'm studying have as their correct answer, including the link that sinear posted.
The first and the 4th are correct. 2nd and 3rd answers are wrong and need to be switched. Instead of reading answers on another exam web site, I prefer reading about the topic on sites that actually describe the issue.
https://www.interserver.net/tips/kb/mac-flooding-prevent/ How to prevent the MAC Flooding Attack? We can prevent the MAC Flooding attack with various methods. The following are some of these methods. 1) Port Security 2) Authentication with AAA server 3) Security measures to prevent ARP Spoofing or IP Spoofing 4) Implement IEEE 802.1X suites 2nd & 3rd answer should be swapped, Mac flooding should be prevented by 802.1x implementation
DHCP Snooping and 80.1x Authenticate are placed in the wrong Attacks, Need to be replaces, Admin Please change the Answers Refer to the links below for further understandings. https://www.interserver.net/tips/kb/mac-flooding-prevent/?__cf_chl_tk=HBU0WjmLQLFAbu4i57fVpxtcHbOHnpJti.oipqw.CyU-1649211364-0-gaNycGzNCJE http://solidsystemsllc.com/prevent-man-in-the-middle-attacks/ https://www.rapid7.com/fundamentals/man-in-the-middle-attacks/
Here is the mapping of the attack mitigation techniques to the types of attacks: | Attack Type | Mitigation Technique | |---|---|---| | 802.1q double-tagging VLAN-hopping attack | Configure the native VLAN with a non-default VLAN ID | | MAC flooding attack | Configure DHCP snooping | | Man in The Middle attack | Configure 802.1X authenticate | | switch-spoofing VLAN-hopping attack | Disable DTP |
I think the original answer is correct. Despite the confusion that 802.1x and DHCP Snooping can mitigate MiTM, however 802.1x is generally considered the strongest and recommended feature for this attack as it provides TRUE individual authentication. https://garykongcybersecurity.medium.com/insecure-802-1x-port-based-authentication-using-eap-md5-c2b298bfc3ab And about MAC Flooding attack, the best way to mitigate it is with port-security, or with DHCP Snooping feature activated, limiting the reception rate, with commands: # ip dhcp snooping limit rate 10 #ip arp inspection limit rate 8 and about "802.1q double-tagging VLAN-hopping." If you use the default native Vlan 1 and the network is using the native vlan for another vlan, and there is traffic from native vlans (without tags) through the trunk ports, and the default native vlan would mistakenly receive this traffic from another native vlan (not default) used on the network.
Implementing IEEE 802.1X suites will allow packet filtering rules to be installed explicitly by an AAA server based on dynamically learned information about clients, including the MAC address. These are the methods often used to prevent the MAC Flooding attack.
given answer is wirong correct answers are the following: * 802.1q double-tagging VLAN-hopping attack = configure the native VLAN with a nondefault VLAN ID * MAC flooding attack = configure 802.1x authenticate * man-in-the-middle spoofing attack = configure DHCP snooping * switch-spoofing VLAN-hopping attack = disable DTP - We can prevent the MAC Flooding attack with various methods including configuration of IEEE 802.1X suites. - Man-in-the-Middle Attacks: In this type of attack, someone tries to intercept and modify the communication between two computers. This can be used to steal sensitive information or inject malicious code into communication. DHCP snooping can detect and prevent these kinds of attacks.
How to prevent the MAC Flooding Attack? We can prevent the MAC Flooding attack with various methods. The following are some of these methods. 1) Port Security 2) Authentication with AAA server 3) Security measures to prevent ARP Spoofing or IP Spoofing 4) Implement IEEE 802.1X suites https://www.interserver.net/tips/kb/mac-flooding-prevent/
To prevent MAC flooding attacks, network operators usually rely on the presence of one or more features in their network equipment: Implementations of IEEE 802.1X suites often allow packet filtering rules to be installed explicitly by an AAA server based on dynamically learned information about clients, including the MAC address. https://en.wikipedia.org/wiki/MAC_flooding